Goal
Enable office-level data isolation so an agent assigned to Office A cannot browse, search, or report on records owned by Office B.
When You Should Enable It
- Multiple branches with distinct P&L or compliance separation.
- Need to reduce accidental data exposure across geographically distinct teams.
- Desire to simplify agent UI (hide irrelevant offices' customers, policies, tasks).
Pre‑Requisites
- All existing agents assigned to the correct office.
- Customer & policy records have an office association (system default if created through standard forms).
- Administrators have validated reporting needs for cross-office metrics (they will retain cross-office visibility).
Key Access Right (How Isolation Actually Works)
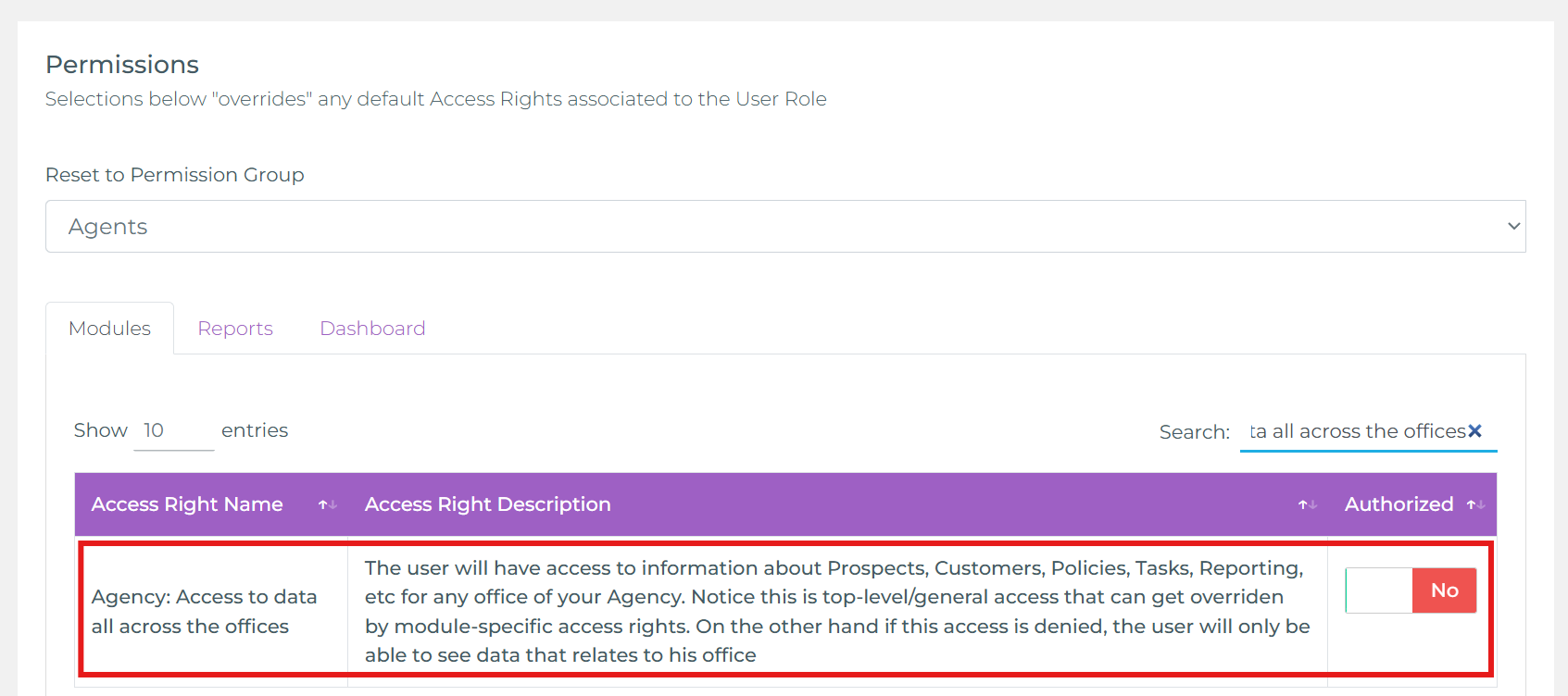
Office isolation is enforced by a single high‑level access right. If the user DOES NOT have the right below, their visibility is automatically restricted to records belonging to their assigned office. Granting the right restores multi‑office visibility (unless other feature‑level rights further restrict a module).
Steps to Enforce Isolation
- Navigate to
Administration > Security > Permission Groups(or open an individual user’s Permissions panel). - Create a new group (top‑right Create Permission Group) if you need a distinct isolated role, or locate and Edit an existing agent group.
- Select (or if creating, name and configure basics for) the permission group applied to agents who must remain limited to their own office (e.g. Agents).
- Use the permissions search box and type part of the access right name (e.g.
across the offices). - Set Agency: Access to data all across the offices to No.
- (Optional tightening) Also set Agency: Access to data related to any agent to No if agents should only see records tied directly to themselves. This pairs with office isolation to become the strictest model. See Agent Visibility Restriction.
- Save / apply the permission group changes.
- Log in (or impersonate) a test agent from Office A and confirm they cannot see Office B’s customers/policies via search, list views, or dashboards. If you also disabled the agent‑level visibility right, verify they only see their own assigned records.
Immediate Effects
- Global searches filtered to agent's office unless user is Administrator or has a cross-office permission flag.
- Customer/policy lists exclude other offices.
- Dashboards reflect only local office metrics for isolated roles.
Audit & Monitoring
Perform a monthly spot check using an agent test account in each office to confirm no cross‑office data bleed. Review access logs for unusual cross-office queries (if available in your subscription tier).
Rollback Procedure
- Open the affected permission group (or user permissions).
- Set Agency: Access to data all across the offices to Yes.
- Save the change; agents inheriting that group immediately regain multi‑office visibility.